Authentication Strengths & Conditional Access with Incode EAM
This article explores how to combine Microsoft Entra ID’s Authentication Strengths and Conditional Access with Incode’s External Authentication Method (EAM). You’ll learn how Incode integrates directly with Entra to act as a trusted external MFA provider, allowing organizations to satisfy Conditional Access requirements using Incode’s secure, frictionless biometric verification.
We’ll break down how Authentication Strengths define assurance levels (e.g., phishing-resistant or federated multifactor), how Conditional Access policies evaluate those strengths, and how Incode EAM fits into the flow. You’ll also find configuration guidance & policy design.
Prerequisites
Configure Incode as a Microsoft Entra External Authentication Method: https://workforce.developer.incode.com/update/docs/entra-external-authentication-method-integration#/
Configuration Guide
-
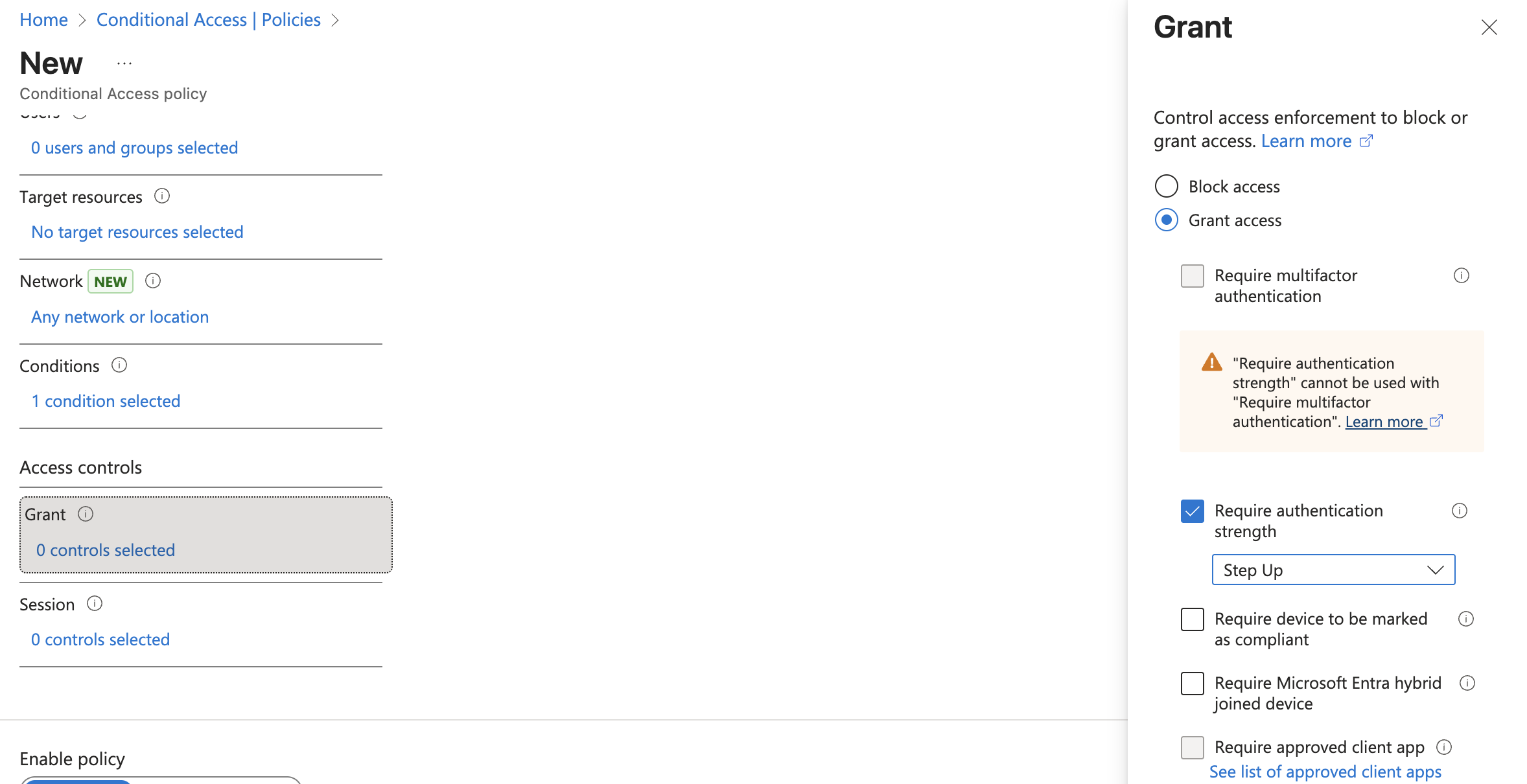
Create Authentication Strength: Go to your Microsoft Entra instance and log in as an administrator. Go to Authentication Methods -> Authentication Strengths and configure the following:
- Select New Authentication Strength
- Enter a Unique Name
- Under Multifactor Authentication select Federated Multifactor
- Click Next
- Click Create
-
Create Conditional Access Policy: Go to your Microsoft Entra instance and navigate to Conditional Access -> Policies and configure the following:
- Select New Policy
- Enter a Unique Name
- Under Users, select the appropriate User and Group Assignments
- Under Conditions, select the Conditions in which you want the Conditional Access Policy to apply
- How to use Conditions in Entra: https://learn.microsoft.com/en-us/entra/identity/conditional-access/concept-conditional-access-conditions
- Under Grant, select Grant Access and select Require Authentication Strength
- Select the Authentication Strength that was configured in Step 1
- Click Select
- Click Create
Test the Integration
- Navigate to a Microsoft Application that meets the Conditions (i.e. https://office.com)
- Enter your Entra Email Address
- Enter your Password
- You'll now be prompted to be redirect to Incode to verify your identity.
- Please note: Entra EAM via Conditional Access policies has a current deficiency that will allow your employees to "Sign in another way" and bypass Incode as a Authentication Method by authenticating with another Factor enrolled on their account.
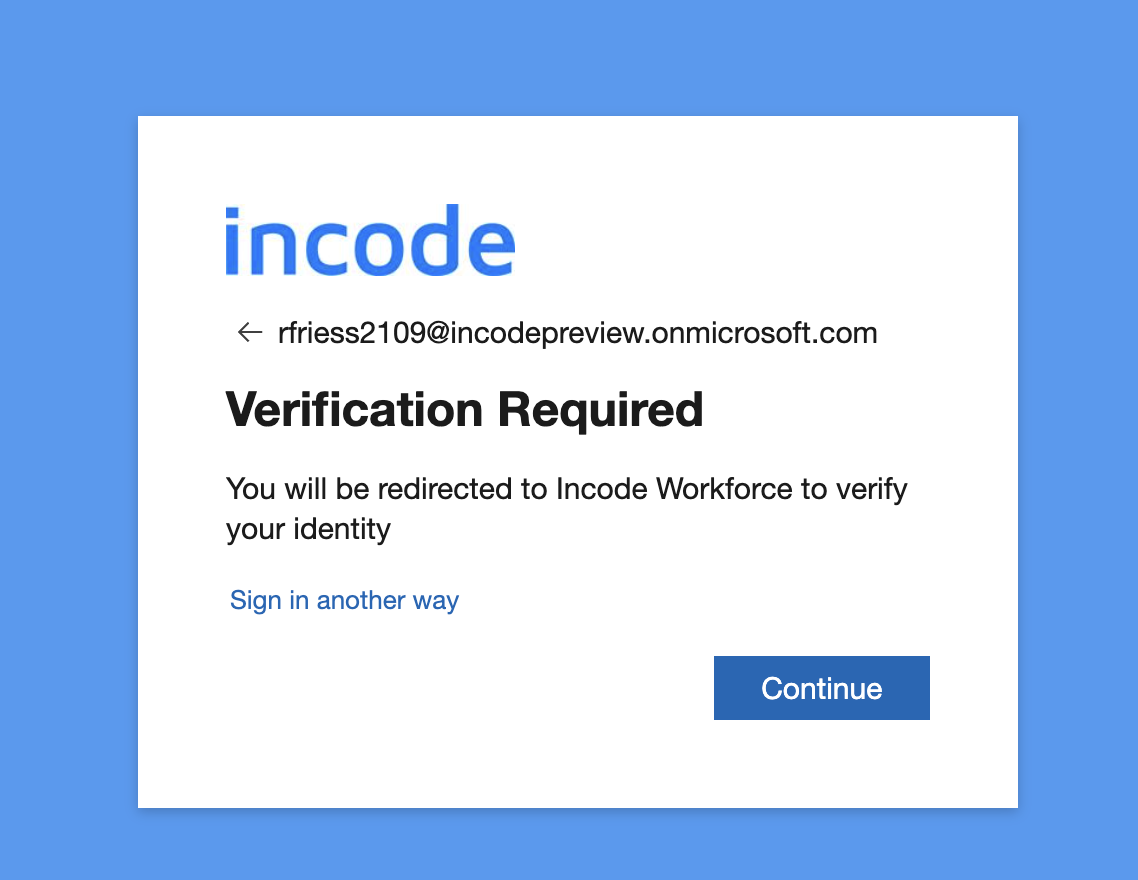
- Select "Continue" and complete the identity verification process.
Updated 3 months ago
