Microsoft Entra as an IAM provider Integration
Before you begin
- Make sure you can access to your company Microsoft Entra instance
- You must have User Administrator, Groups Administrator, Application Administrator and App Developer role to perform App Registration, group and user setup
- You must have Global Administrator role to grant required App permissions
- You must add mandatory data to employee profile
If your Microsoft Entra has federated access through another IAM provider, such as OKTA, then you should follow steps in OKTA INTEGRATION GUIDES
User profile configuration requirements
Incode Workforce reads data from Microsoft Entra user profile. Depending on Claim matching policy configuration, some of the following fields in Entra user profile may be mandatory in order to perform identity verification:
- First Name: User's first name (or Given name)
- Last Name: User's last name (or Surname)
- User principal name: User's login
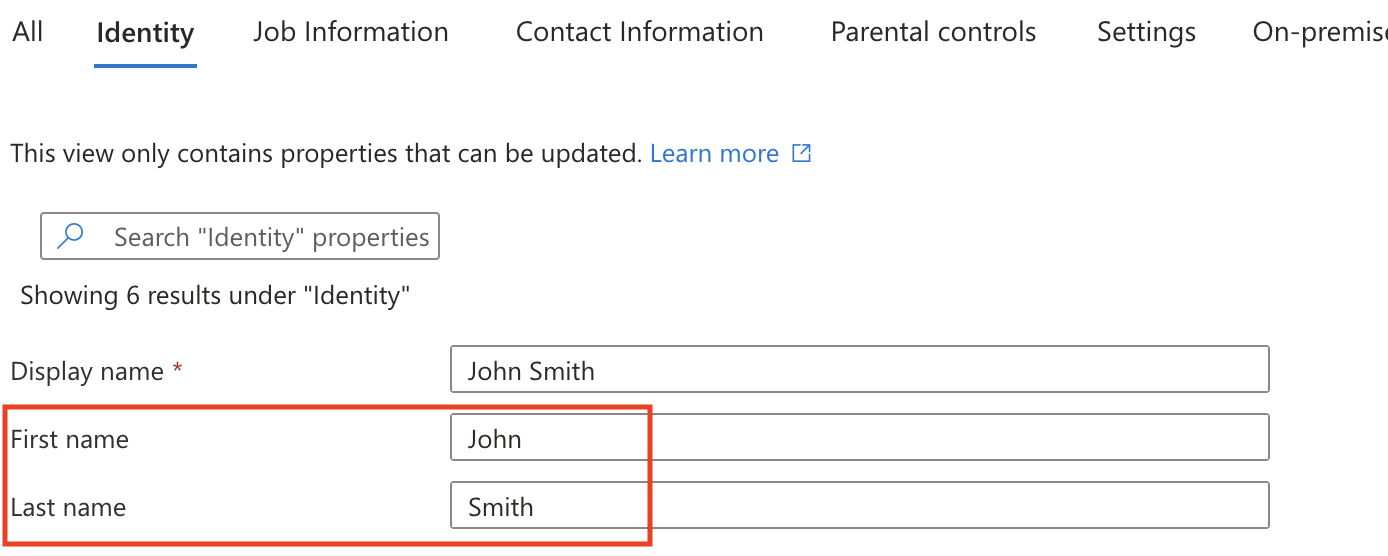
Fill out First and Last name for all users in your employee directory
-
Street address: Residential address
-
City: Residential city
-
State or province: Residential state (where applicable)
-
ZIP or postal code: Residential postal code
-
Country or region: Residential country
-
Mobile phone: Primary phone number
-
Email: User's work email. This is the email user will be receiving registration information.
-
Birthday: Date of birth
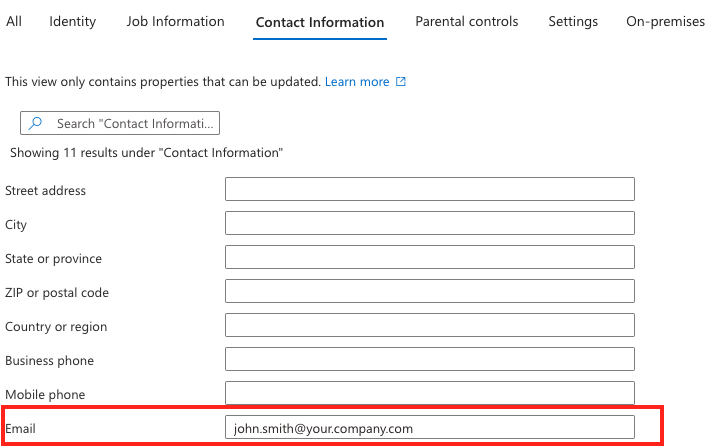
Fill out Email field in user Contact information
Make sure that all users in the group of employees who need to leverage Incode identity verification have these fields correctly setup.
Workforce IAM Settings for API Access to employees directory
The Workforce product needs to sync with your employee directory to ensure only active employees can complete verifications. It also syncs to the employee directory to enable password / MFA resets at user's request. This is achieved through an (automated) App integration which has minimum necessary data scopes.
Workforce configuration
Provide User group id in the Workforce Dashboard in the Settings -> IAM Settings. This is a user group id (Object Id) that you want to assign Workforce. Usually, it is an all employees group. To find user group id go to your Microsoft Entra portal -> Groups -> All groups and copy Object id for group you want to use.
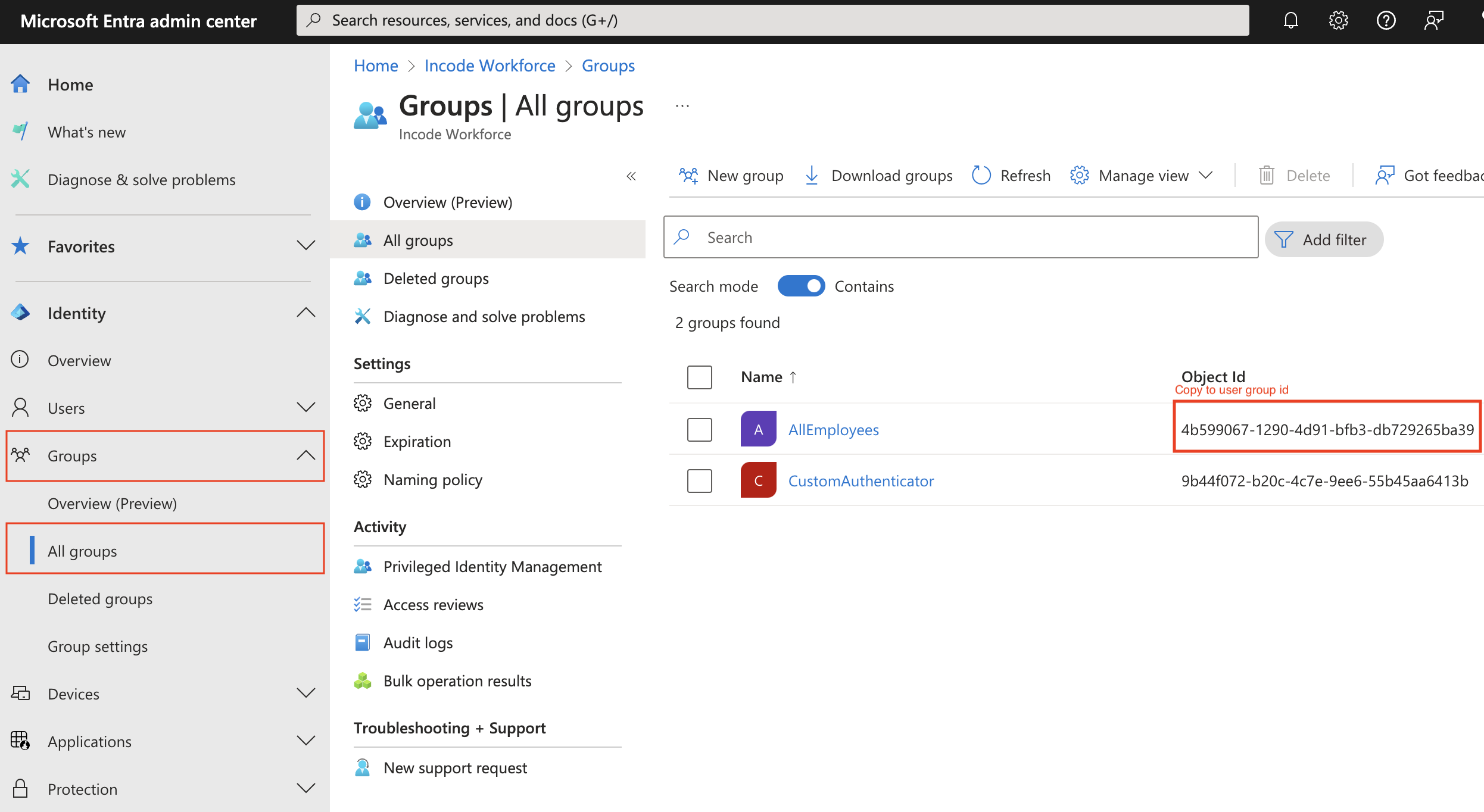
Find user group id in your Microsoft Entra portal
Save settings. You will be redirected to Entra admin consent page, to approve required permissions. Once that is completed, you will be redirected back to Settings page in Workforce. You are ready to test identity verifications on request or password/MFA resets.
Note: If the permissions are rejected, or you do not possess enough sufficient privileges to approve them, IAM configuration will remain in incomplete state, in which case it can be deleted and the process needs to be restarted.
Test. Trigger Directory Sync to make sure everything is connected successfully. Depending on the size of your employee directory it might take some time to import all employees into Workforce. Go to Helpdesk Verification and choose employee to whom you want to send verification request. A list of all employees from the group you have configured in the IAM settings will be displayed. To test password or MFA reset, go to Self-serve portal. Once user's identity is verified, they can reset password or MFA. Next time user logs in into Microsoft Entra they will be asked to setup a new password or configure authentication factors.
Updated 5 months ago
