Microsoft Entra Integrations
Incode Workforce Integration with Microsoft Entra
Incode integrates with Microsoft Entra to provide high-assurance identity verification for employees. It’s used for Self-Service Password Reset (SSPR), MFA recovery, and as an external authentication method step to gate sensitive access.
Key capabilities
- SSPR & MFA recovery – Redirect users who forgot a password or can’t satisfy MFA to Incode for biometric/document verification.
- External authentication – Add Incode as a high-assurance check before granting access to apps or workflows.
- New-hire onboarding – Verify legal identity prior to activating Entra credentials.
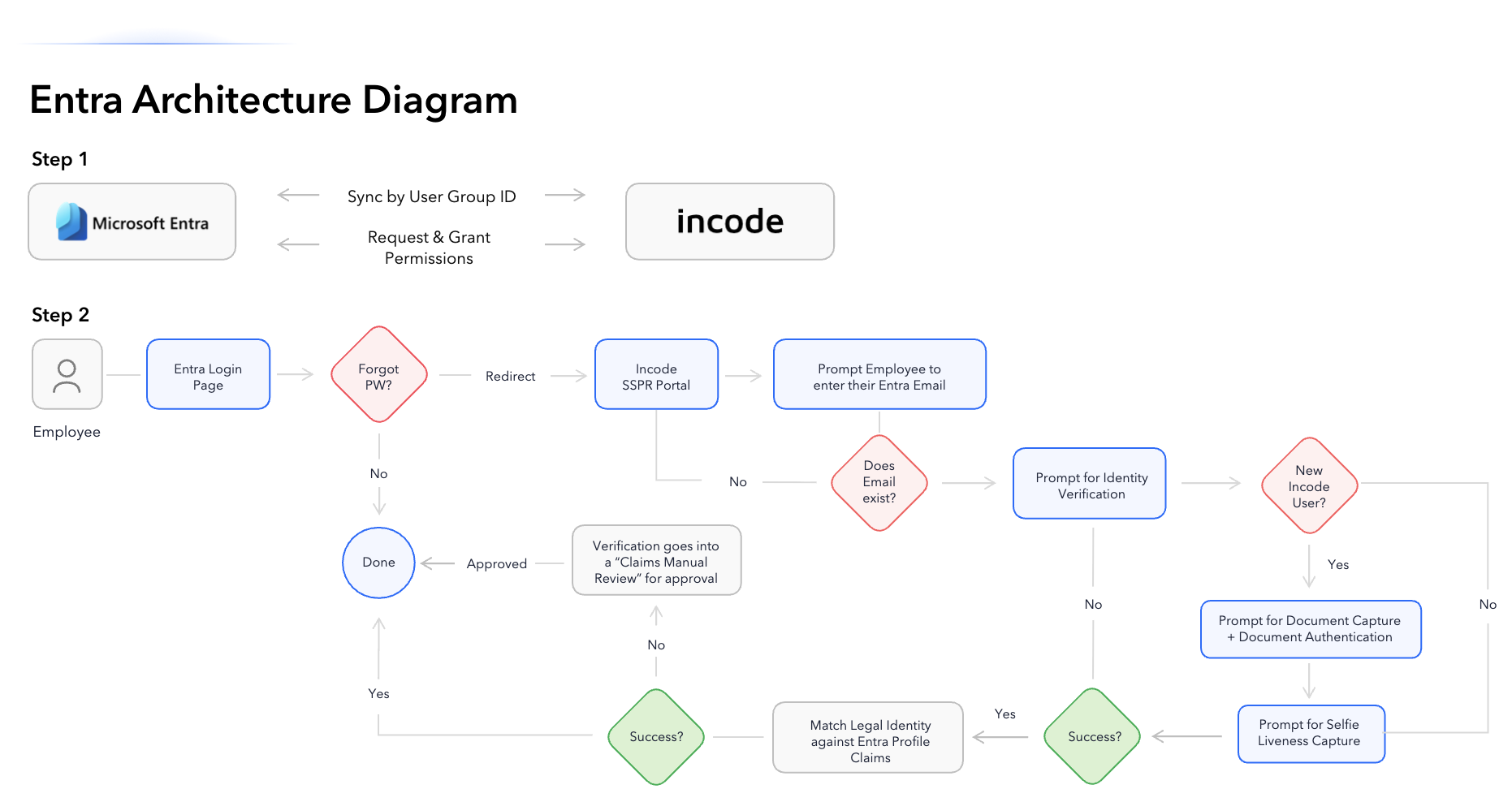
Architecture
-
Directory sync & permissions
- Grant Incode read permissions to the Entra directory.
- Sync User/Group IDs needed to locate users and enforce policy.
-
Claims matching against legal identity
- Incode verifies the user’s government ID and live selfie.
- Verified attributes are matched to Entra profile claims before approving SSPR/MFA recovery or onboarding.
End-user flows
Password reset & MFA recovery (SSPR / MFA Reset)
- User selects Forgot password (or fails MFA) on the Entra login page.
- Entra redirects the user to the Incode Self-Service Portal.
- User enters their corporate email; Incode checks if it exists in Entra.
- User completes document capture and selfie liveness.
- Incode matches verified attributes to Entra claims.
- Success: Entra allows SSPR/MFA recovery.
- If not matched: case is routed to claims manual review for approval.
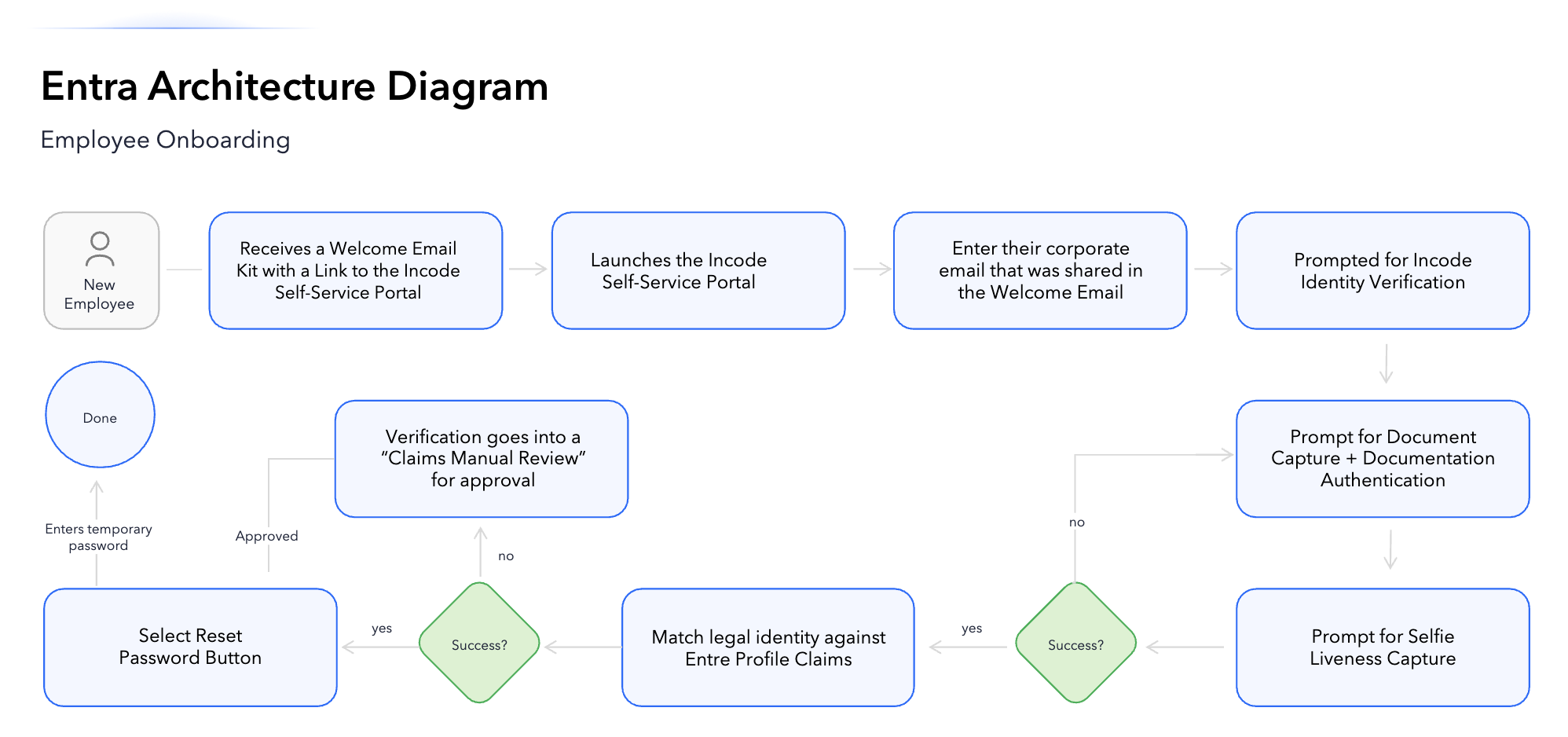
New-hire onboarding
- New employee receives a Welcome email with a link to Incode.
- User verifies identity via document + selfie.
- Incode matches legal identity to Entra profile claims.
- On approval, the user sets a temporary password and completes onboarding.
User profile configuration requirements
To enable reliable claims matching, we recommend these Entra attributes be populated and accessible to Incode:
- Email/UPN (primary lookup key)
- Given name and Surname
- Date of birth (optional: if your directory stores it)
- Group/Role membership (for policy and routing)
- Tenant/Directory ID (for scoping)
- Optional: Phone number and Secondary email (for notifications)
Note: Exact attributes can be adapted to your schema; the goal is to have a stable identifier that can be cross-verified with the user’s legal identity.
Updated 4 months ago
